Control systems are at the foundation of today’s industrial applications, and are certainly nothing new. They drive critical infrastructure, from the power grid to factories to transportation systems. And along with the many millions of devices that connect to the Industrial Internet of Things (IIoT), proper security measures must be put in place to protect them.
The trick when implementing security, however, is that you do not want it to compromise the function and fundamental requirements of the system, such as reliability, real-time performance, autonomy and interoperability.
A white paper from Real-Time Innovations (RTI) explains that control systems designed for use in the IIoT are highly distributed in nature. A typical control system will need to synthesize live data streams from numerous sensors, actuators and other connected devices. Processed data, the paper describes, “then drives device control, and feeds other subsystems relating to operator interfaces, back-end systems, IT and cloud applications.”
“Because of their hierarchical nature, many modern control systems are referred to as “systems of systems.”” the paper continues. “These highly complex systems, with smarter devices at the lower levels and broadened information sharing at the upper levels, pose unique security challenges. System designers must meet those challenges without compromising other vital requirements relating to real-time performance, safety and reliability.”
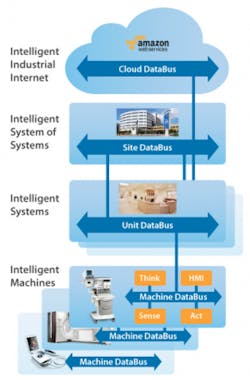
The figure to the right shows that within a modern hospital, for example, the Industrial Internet connects intelligent medical devices at the bedside, in operating rooms and throughout all departments. The applications that aggregate data from these devices are themselves part of larger systems that drive up overall quality of care and save lives. Safeguarding patient health information and ensuring continuity of care requires security at every level of the hierarchy.
The paper goes on to show what it calls the four keys to securing the IIoT and provides an analysis of the requirements of each:
- Decentralized architecture
- Access control
- Elimination of TCP/transport layer dependencies
- Interoperability
To learn all the details, download the full RTI paper, “Four Keys to Securing Distributed Control Systems” from our Content Library.