The Industrial Internet of Things (IIoT) represents the biggest opportunity in recent decades for the advancement of industrial technology. Major global companies are transforming their infrastructures to take advantage of the Industrial Internet’s open, high-bandwidth protocols and low-cost, intelligent networks.
In the oil and gas industry, innovative networking standards and protocols brought about by the IIoT are enabling revolutionary system-building approaches that greatly ease field operations.
At the same time, however, the oil and gas industry is facing challenges caused by the massive data flowing from new sensor technology, new analysis techniques, complex drilling processing, changing requirements and regulations for well monitoring and reservoir management and other industry trends that call for innovative solutions.
To address all of these industry changes, companies need to embrace more intelligent systems and processes. The Industrial Internet, which facilitates building smart, distributed systems, offers a foundation for taking real-time data and using it to drive more intelligent, safer operations with more automated oversight.
At the core of the Industrial Internet are several protocol standards, one of which is the Data Distribution System (DDS) published by the Object Management Group (OMG). (See a comparison of protocol standards) In a recent whitepaper, RTI (Real Time Innovations) provided five use-cases demonstrating how their use of DDS proved beneficial in solving challenges faced by the unique needs of the oil and gas industry
A DDS security model, the paper explains, “allows protection of every dataflow. This “per-topic” security is logically simple: the DataBus connects information sources to information sinks. The security model simply enforces the connections by authenticating endpoints and allowing only the configured communications. The protocol supports discovery authentication, data-centric access control, plug-in cryptography, tagging/logging, and secure multicast – in a 100%-standards-compliant manner.”
This security breach detection system demonstrates both protection of a previously-insecure link and detection of many attack vectors through simple scripted analytics.
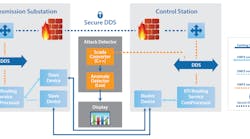
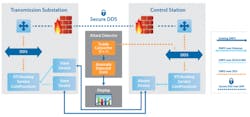
In a Pacific Northwest National Laboratory (PNNL) use case, for example, RTI introduced a DDS solution to both protect data flows and detect anomalies between a transmission substation and a control station. They replaced a legacy, insure protocol connection with a Secure DDS connection and wrapped messages in the legacy protocol as Secure DDS messages. These messages where then sent from substation to control station, thus implementing a secure, protected link.
According to the paper, a truly robust security plan requires both protection (stopping unwanted activities) and detection (finding and reporting when the protection has been compromised). For the detection leg of this system, a data tap was installed in the secure control center. By monitoring both the “meta data” (who is connected, speed of connection, etc.) and the actual data flow, simple security scripts were able to detect various types of attacks.
The other four use cases give information on automated well drilling, intelligent well monitoring, real-time reservoir management, and asset tracking. Download “Five Ways the Industrial Internet is Changing the Oil and Gas Industry.”
Check out more infrastructure technologies white papers in our Content Library.