Stopping ransomware & protecting critical infrastructure is easier than you might
By David Levine, director solution consultant of Remediant
From a cybersecurity standpoint, the past few months have been busy for the industrial and manufacturing sector. Amid looming cybersecurity threats on industry, the FBI alert on the recent BlackCat/ALPHV ransomware that victimized German oil companies and Swissport is just the latest evidence that critical infrastructure will remain a focus for cybercriminals looking to strike fear and cause chaos.
While terrifying, the increase we're seeing in ransomware groups like BlackCat attacking the supply chains and industrial companies is not surprising. Ransomware often hits industrial control systems (ICS) or other operational technology (OT) environments with significant impact; both government and security groups have been warning organizations that ransomware poses an increasing threat to ICS.
How BlackCat ‘bites’ its victims
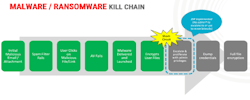
The BlackCat/ALPHV ransomware incident leverages previously compromised user credentials to gain initial access to the victim's system. Once the malware establishes access, it compromises Active Directory user and administrator accounts. The malware uses Windows Task Scheduler to configure malicious group policy objects (GPOs) to deploy ransomware. Initial deployment of the malware leverages PowerShell scripts, in conjunction with Cobalt Strike, and disables security features within the victim’s network. In fact, all cyberattacks follow the Cyber Kill Chain blueprint as illustrated below:
Credit: Identity Defined Security Alliance (IDSA)
The solution? It’s easier than we think
While President Biden signed an executive order calling for a complete reformation of supply chain cybersecurity standards throughout the government and private sectors, and it’s hopeful to see the administration is taking these threats and attacks seriously, the industry needs to be proactive in protecting its assets. Mitigating threats from the majority of ransomware, like BlackCat, can be as easy as establishing a proper privileged-access-management program. It requires a methodical approach—despite discovering and vaulting the most coveted accounts, it’s essential to look at standing privileges across the estate and follow industry best practices, which include a critical idea dubbed Zero Standing Privileges (ZSP). ZSP as part of the Zero Trust model is the most secure way to mitigate lateral-movement threats.
The idea of ZSP is simple: remove the 24x7x365 login rights of all privileged accounts from all servers, workstations, and laptops. You leave standard users as is, but when it comes to privileged access, it should be enabled with just-in-time-access (JITA). JITA is the cornerstone of ZSP. A user requests access to a specific machine, at a specific time and only for a specific period of time. This way, even if a user’s credentials are compromised, the blast radius is reduced to one system, or worse, just a handful of systems that the same user requested JITA access as opposed to hundreds or thousands of systems where the user had standing privileges.
As headlines continually show us, managing your standing privileges is one of the most critical and effective methods to prevent lateral movement and halt most incidents. The longer you wait to address it, the greater your chances of becoming a headline.