By Mrugesh Chandarana, director product management, identity and access-management solutions, HID Global
The pandemic has changed so much about how people travel, work, and make purchases. Manufacturing organizations have also been affected, leading them to adopt hybrid work environments where there is even greater need for a “digital signature” to help protect software code or documents.
Digital assets are still at risk, however, since people can make a signature’s expired or revoked certificate appear as though it were still valid. An important way to combat these certificate changes and forgeries is timestamping services that bring trust to digital signatures.
Why digital signatures are at risk
Digital signatures are used with everything from Computer Aided Design (CAD) and other engineering documents and technical documentation to software applications and the daily flow of proposals, agreements, contracts, financial reports, and other documents.
To understand how these digitally signed documents are at risk, one need only consider the workflow for a traditional ink signature. Any time a legal document is signed, it is typically with a notary present to verify the identity of the person who is signing and validate the date and time of the signature. The signature is recorded in a logbook with the date and time of the transaction and a thumbprint.
This flow has been approximated in the digital world. Documents are signed with a public key infrastructure (PKI)-based digital signature, followed by a non-repudiation step. For example, when a PDF document is digitally signed with a PKI based certificate, it adds information about the person and date and time of the signature. However, this date and time can be manipulated or forged, since the computer’s local time upon which it is based can be changed or forged. If the certificate is expired or revoked, a person could potentially make it look valid by changing this local computer time.
To trust the digital signature, one also must be able to trust the timestamp.
Benefits of trusted timestamping
PKI digital certificates are used to create trusted digital identities for many use cases such as authentication, data encryption, document or code signing. The Internet Engineering Task Force (IETF) PKI Time-Stamp Protocol (TSP) goes further to establish the digital signature’s “proof of existence” at an instant in time. Trusted time stamps combat digital-certificate forgery, prevent unauthorized use of revoked certificates, simplify time-based compliance record-keeping, strengthen legal claims, and prove long-term signature validity. Application examples include securing antivirus software updates with timestamped signatures.
A timestamping authority must meet IETF standards RFC 3161 requirements and use the PKI TSP to apply an accurate, trusted timestamp to a digital signature. This timestamp is used to guarantee data integrity and prove that the data has not been tampered with. Using this type of trusted timestamp when signing a document or code prevents tampering.
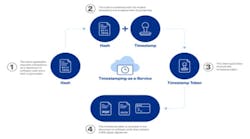
First, the timestamping authority uses PKI to apply a timestamp to the document or code. Following are the steps:
- The client application such as Microsoft Authenticode or Signtool creates a hash of the document or code file and sends it to the timestamping authority.
- The timestamping authority combines the hash of the file and with a trusted timestamp and signs it with a private key. Next, it creates a timestamp token, which is returned to the client.
- The timestamp token is recorded within the file.
There are use cases, such as antivirus signature file-signing or firmware-signing, which require high throughput of millions of timestamps per week. Trusted timestamping service providers use this process to provide enterprises with a high-availability cloud-based platform for embedding timestamps to any software application, documents, or digital files. If the timestamp file is manipulated after the signature and timestamp are applied, the hash value will not match, the file’s seal is broken, and the user is alerted that the file is no longer in its original state—the data is altered and it can no longer be trusted.
Trusted timestamping is seeing growing adoption among users who need to verify the date and time of their electronically or digitally signed documents, code and other files. It can prevent forgery and create longevity for these digital signatures (even after expiration) by providing long-term validation and non-repudiation of their time and date.